In 2015, Lahey Hospital and Medical Center agreed to pay $850,000 to the U.S. Department of Health and Human Services following a HIPAA investigation into a 2011 laptop theft. The stolen laptop, connected to a CT scanner and taken from an unlocked treatment room, contained unsecured electronic protected health information (ePHI) of 599 individuals. The Office for Civil Rights alleged serious compliance failures, including a lack of risk analysis, inadequate workstation safeguards, and the absence of activity tracking. Lahey entered a two-year corrective action plan requiring risk assessments, updated HIPAA policies, staff training, and monitoring, underscoring the need for strong security and encryption.
NIST 800-88: Complete Guide to Media Sanitization & Secure Data Erasure

TL;DR: NIST 800-88 Everything You Need To Know
-
Gold Standard for Data Erasure NIST 800-88 is the globally recognized guideline for making data on HDDs, SSDs, mobile devices, and other storage media completely unrecoverable. It helps protect enterprises from breaches, fines, and reputational damage.
-
Three Sanitization Levels. It defines Clear, Purge, and Destroy methods, each suited to different data sensitivity levels, with rigorous verification requirements to ensure no residual data remains.
-
Verification and Certification. NIST compliance requires proof, including audit-ready certificates with device details, methods used, and verification results. This is critical for industries like healthcare, finance, and government.
-
Environmental and Operational Benefits. When paired with Clear or Purge, organizations can securely reuse, donate, or resell devices, cutting e-waste and supporting ESG commitments while staying compliant.
-
How Workwize Helps. Workwize uses NIST 800-88 compliant erasure workflows into enterprise IT asset offboarding, ensuring every decommissioned device is securely sanitized, verified, and documented. This streamlines compliance and reduces risk across global operations.
Why NIST 800-88 Matters for Data Security
When a hard drive, SSD, or mobile device reaches the end of its useful life, what happens to the data stored on it?
For enterprises, this question is more than operational—it’s a matter of security, compliance, and reputation. The wrong answer can lead to regulatory fines, brand damage, and exposure of sensitive information.
This is where NIST 800-88, the U.S. government’s gold-standard guideline for media sanitization, comes in. Published by the National Institute of Standards and Technology, NIST 800-88 offers a clear, adaptable framework for rendering data irretrievable, whether the media in question is an old server drive, a stack of USB sticks, or a cloud storage migration backup.
For organizations navigating tight compliance mandates and stringent cybersecurity standards, understanding and applying NIST 800-88 is no longer optional. It’s a critical safeguard against data breaches in an era where attackers will happily sift through discarded hardware to find their next opportunity.

What is NIST 800-88?
NIST 800-88, officially titled “Guidelines for Media Sanitization,” was first released in 2006 and updated to Revision 1 in 2014. Its purpose is straightforward: to provide methodical, technology-agnostic instructions for erasing data from any type of electronic storage media.
While it originated in U.S. federal government operations, its adoption has spread worldwide. It’s now the benchmark for private sector data destruction, surpassing older standards like DoD 5220.22-M, which hasn’t kept pace with modern storage technologies such as SSDs.
The scope of NIST 800-88 is intentionally broad. It applies to:
-
Magnetic storage (HDDs, tapes)
-
Solid-state drives (SSDs)
-
Flash media (USB drives, SD cards)
-
Mobile devices
-
Data center storage systems
-
Any future storage technology that may emerge
Its reach even extends to international frameworks, with principles incorporated into standards like ISO/IEC 27040:2015. This universality makes it the de facto global playbook for secure media sanitization.
🔥Workwize Delivers Secure Data Erasure & Disposal
- Certified Wipes: Apple DFU restores, Windows USB reinstalls, or Blancco NIST-compliant erasure for 100% data removal.
- Proof of Security: Receive a wipe certificate for every device to satisfy audits and compliance checks.
- Global Compliance: Fully aligned with local data protection laws in every region we operate.
- Resale for ROI: Partner with ITAD vendors to resell your retired devices, turning old assets into credits for your account.
- Eco-Responsible Disposal: Reduce e-waste with responsible recycling and circular hardware flow.
- Custom Wipe Options: We can validate and execute your preferred data erasure process while maintaining SLAs.
- End-to-End Management: From retrieval to resale or recycling with no manual coordination required.
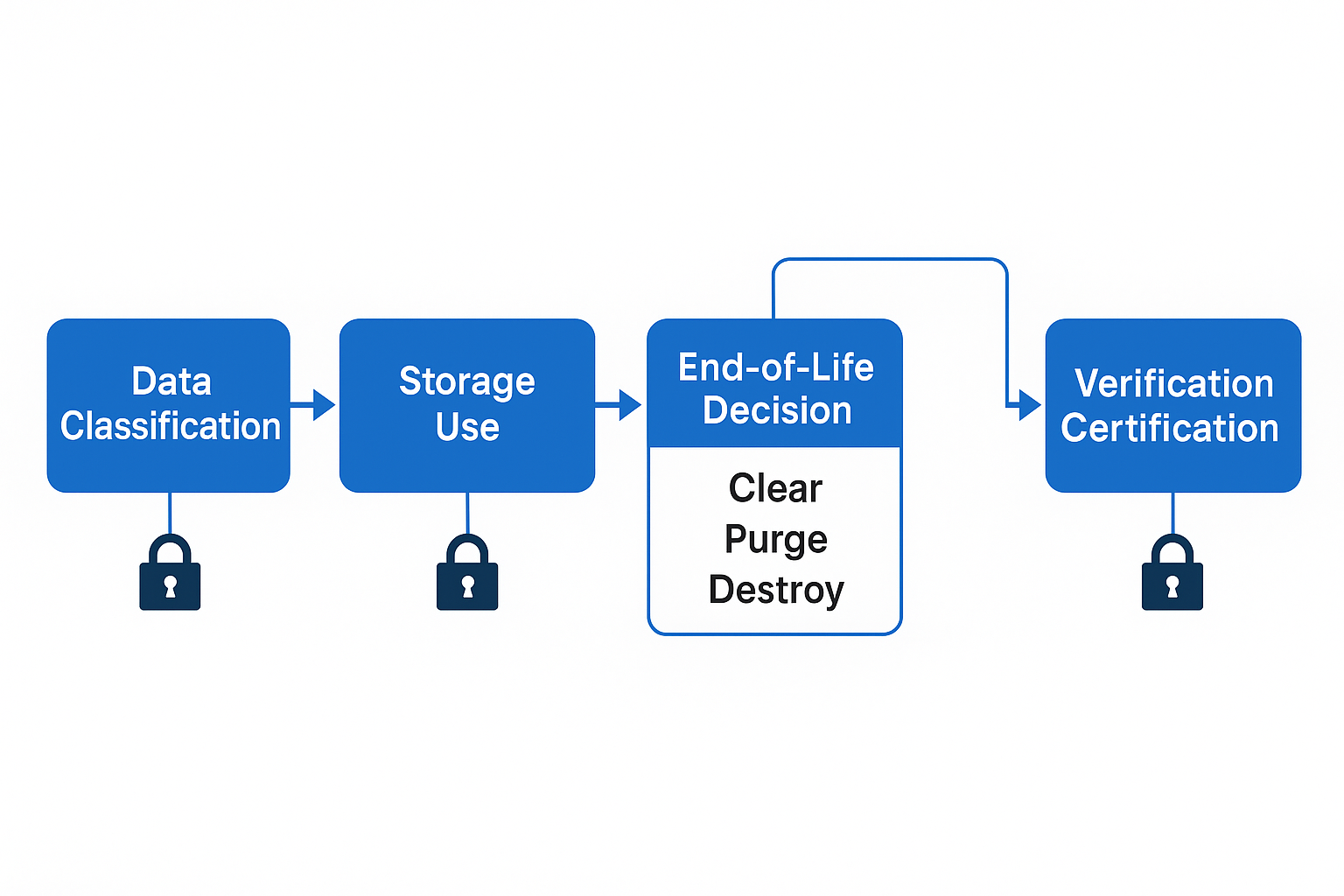
Key Principles of Media Sanitization
At the heart of NIST 800-88 is the concept of “sanitization”: making data access infeasible for a given level of effort. The guidelines stress that this process must be built into the entire data lifecycle—not just as an afterthought when decommissioning assets.
NIST recommends organizations begin with:
-
Data classification: Identify confidentiality levels for all stored data.
-
Media type assessment: Understand how data is stored physically and logically.
-
Risk evaluation: Weigh the potential impact if data were to be recovered.
-
Future use determination: Will the asset be reused internally, donated, sold, or destroyed?
Other considerations include cost, environmental impact, and available technology. In practice, this means choosing the right sanitization method early—so that when a device reaches end-of-life, the process is efficient, auditable, and airtight.
The Risks of Inadequate Data Sanitization
Data security often fails at its weakest point—and for many organizations, that’s during asset disposal. When devices change hands without proper sanitization, residual data can remain accessible. Attackers know this, and some deliberately target second-hand markets, recycling streams, or improperly disposed drives.
Real-World Breach Examples
-
-
In 2019, Morgan Stanley faced reputational damage when a third-party IT Asset Disposition (ITAD) vendor failed to properly wipe SSDs and other hardware.
Devices from data centers and branch offices, containing unencrypted client financial data, were improperly sold or went missing. The issue traced back to vendor Triple Crown, which passed hardware to another recycler without secure erasure. And then a similar 2016 incident compounded the problem.
The U.S. Office of the Comptroller of the Currency fined Morgan Stanley $60 million for inadequate oversight, and the bank reached a class-action settlement, underscoring the critical need for strict ITAD vendor management and verification.
-
In November 2022, four SSDs went missing from SAP’s Walldorf, Germany, data center despite being stored in a “secure location.” They were moved to an unsecured building, from which they were taken without permission. Months later, an SAP employee found one of the disks for sale on eBay and purchased it as part of an internal search. The recovered drive contained personal records of about 100 employees, though SAP stated no customer data was compromised. The other three drives remain missing. This marked the fifth similar European data center incident in two years, highlighting risks from poor asset security and disposal.
In each of these cases, the breach was not due to advanced cyberattacks—it was caused by inadequate data sanitization.
4 Common but Outdated Data Sanitization Methods
Over the years, several techniques have been used to erase data. Many still circulate in ITAD workflows, but they often fail to meet NIST’s modern requirements.
Degaussing
Once a staple for magnetic media destruction, degaussing uses a strong magnetic field to erase data. While effective for older HDDs, it does nothing to SSDs and many modern high-coercivity drives.
Overwriting
Overwriting replaces existing data with patterns of random or fixed values. On traditional magnetic drives, one pass can be sufficient. However, it fails to address unallocated areas, hidden partitions, or defects—and SSD wear-leveling can leave data untouched.
Shredding
Physical destruction methods like shredding, pulverizing, or incinerating can destroy media entirely. But with today’s high-density chips, standard shred sizes may leave recoverable fragments. Physical destruction also eliminates reuse potential and carries environmental costs.
Encryption Alone
Encrypting drives and then deleting keys can render data inaccessible, but only if all keys are truly destroyed. Verification is challenging, and encryption is not a complete sanitization process under NIST guidelines unless combined with other methods.
NIST 800-88 Sanitization Categories
NIST 800-88 divides sanitization into three main categories, each suited to different data sensitivity levels.
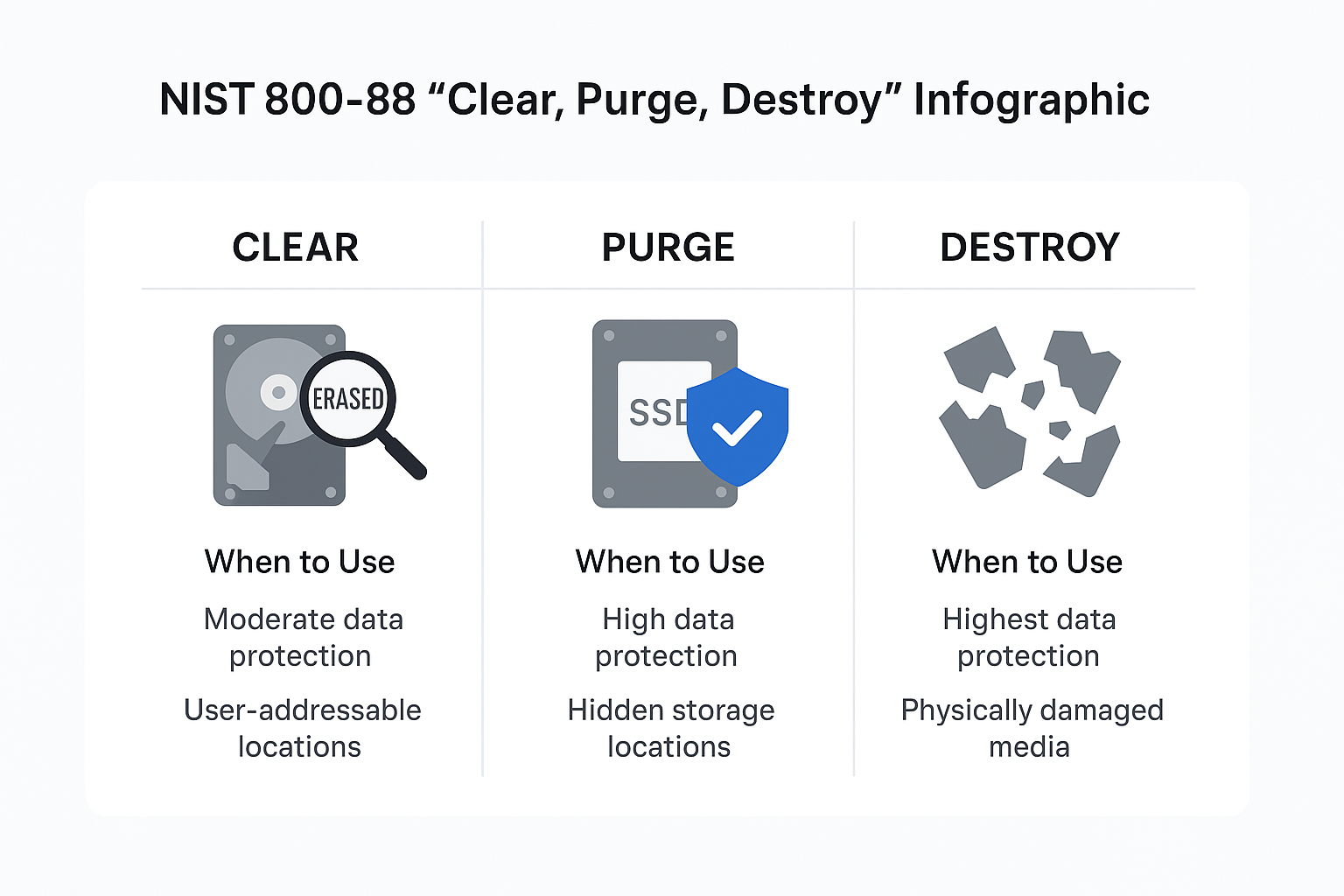
Clear
Logical techniques are applied to all user-addressable locations, protecting against basic recovery tools. This is often done via overwriting or factory resets. Best for lower-sensitivity data.
Purge
More advanced physical or logical techniques that protect against sophisticated recovery, including from hidden areas like Host Protected Areas (HPA). May involve firmware commands, block erase, or crypto erase. Suited for high-confidentiality data.
Destroy
Physical destruction renders the media completely unusable. Methods include shredding, incineration, or melting. Necessary for irreparably damaged drives or highly classified data where reuse is impossible.
For maximum security, some organizations combine Purge with Destroy.
Step-by-Step Workflows for NIST Methods
Clear Workflow
-
Identify all user-accessible storage areas.
-
Overwrite with random or fixed data patterns.
-
Verify overwrite completion via software logs.
-
Issue certificate of sanitization.
Purge Workflow
-
Remove hidden areas (HPA/DCO).
-
Trigger firmware-based block erase or crypto erase.
-
Conduct forensic-level verification.
-
Document and certify process.
Destroy Workflow
-
Choose destruction method (shredding, incineration).
-
Reduce to approved particle size.
-
Dispose of waste via certified e-waste channels.
-
Maintain destruction logs and certificates.
Understanding Cryptographic Erasure in NIST Guidelines
Cryptographic Erasure uses encryption as a sanitization tool—encrypting all stored data, then securely deleting the encryption keys. Without the keys, the data becomes unreadable.
NIST recognizes this method but stresses:
-
Keys must be irreversibly destroyed.
-
Verification is essential.
-
It works best when encryption is native to the device and properly managed.
For SSDs, crypto erase can be faster and less resource-intensive than physical destruction, making it a valuable tool in enterprise workflows.
Verification: The Cornerstone of NIST Compliance
No matter which method is used, NIST emphasizes verification as non-negotiable. Verification ensures that data is not just erased in theory, but truly unrecoverable in practice.
Two approaches are outlined:
-
Every instance verification: Confirming each piece of media is fully sanitized.
-
Representative sampling: Testing a subset of media, ideally by personnel not involved in the erasure.
Verification may involve forensic testing, read-back analysis, or automated validation from certified erasure software.
Without verification, even well-intentioned processes can leave dangerous gaps.
Generating an Audit-Ready Certificate of Data Erasure
For compliance purposes, proof matters. An audit-ready certificate documents:
-
Device serial numbers
-
Sanitization method (Clear, Purge, Destroy)
-
Tools used
-
Verification results
-
Date and operator details
This certificate is essential for industries governed by strict regulations, including healthcare (HIPAA), finance (GLBA), and defense (CMMC). It provides a defensible record in case of audits, breaches, or regulatory inquiries.
NIST vs. Other Data Erasure Standards
|
Standard |
Strengths |
Weaknesses |
Best Use |
|---|---|---|---|
|
NIST 800-88 |
Technology-agnostic, modern media support, verification emphasis |
Requires expertise and tools |
Enterprises, government, ITAD |
|
DoD 5220.22-M |
Well-known, easy to implement |
Outdated, SSD limitations |
Legacy HDD wiping |
|
ISO/IEC 27040 |
Global applicability, storage security scope |
Less detailed on sanitization |
Multinational compliance |
|
GDPR Erasure Requirements |
Legal backing, user rights focus |
No technical method guidance |
EU data privacy enforcement |
Environmental and Cost Considerations in Media Sanitization
Physical destruction is final; it also creates waste and eliminates the chance to reuse or resell devices. In an era where ESG commitments matter, many enterprises prefer Clear or Purge to extend hardware lifecycles.
Reuse within the organization or donation to nonprofits can generate cost savings, reduce e-waste, and support corporate sustainability goals—provided sanitization meets NIST standards.
How NIST 800-88 Applies to Industry
-
Healthcare: Ensures HIPAA compliance when decommissioning medical devices and storage systems.
-
Financial Services: Protects sensitive account and transaction data from unauthorized recovery.
-
Government Agencies: Meets strict confidentiality requirements for classified or sensitive information.
-
Enterprise IT: Streamlines secure hardware refresh cycles while maintaining audit readiness.
How NIST 800-88 Integrates with International Standards
While NIST 800-88 is a U.S. standard, its influence is global. Its principles appear in:
-
ISO/IEC 27040:2015 (storage security)
-
European GDPR data protection requirements
-
APAC data privacy frameworks
For multinational enterprises, aligning with NIST 800-88 creates a common compliance baseline across geographies.
Implementing NIST 800-88 in the Enterprise
Adopting NIST 800-88 isn’t just about ticking a compliance box—it’s about embedding secure data handling into operational culture. Key steps include:
-
Classifying all data assets.
-
Mapping current sanitization workflows.
-
Identifying compliance gaps.
-
Choosing certified tools and partners.
-
Training staff on NIST methods and verification.
Protecting Data from Creation to Destruction
In a world where data breaches can originate from discarded devices, NIST 800-88 offers a clear, adaptable, and globally respected framework for secure data erasure. Selecting the correct method—Clear, Purge, or Destroy—and combining it with rigorous verification, organizations can close one of the most overlooked security gaps in their infrastructure.
Whether you’re refreshing a data center, migrating to the cloud, or decommissioning hundreds of laptops, NIST 800-88 ensures that your data leaves no trace behind.
FAQ: NIST 800-88 and Data Sanitization
Q1: Is NIST 800-88 legally required?
Not always, but it’s mandated for U.S. federal agencies and often required by contracts and compliance frameworks.
Q2: Does NIST 800-88 apply to SSDs?
Yes—it includes specific guidance for solid-state media, unlike older standards.
Q3: How is NIST different from DoD wiping methods?
NIST is more modern, covers a wider range of media, and includes verification requirements.
Q4: Can I meet GDPR erasure requirements with NIST 800-88?
Yes—NIST-compliant erasure supports GDPR’s “right to erasure” by providing proof that data is irretrievable.
About the authors:
Simplify IT operations with Workwize
Learn how Workwize makes IT asset management easier and more efficient. Schedule a custom demo today and see the difference.
Recent articles
NYDFS 500.13 Compliance: How Workwize Simplifies Asset Management and Data Retention
November 1, 2025: Financial Institutions Must Meet NYDFS 500.13 Compliance on Asset...
Data Wiping 101: Benefits, Methods, Considerations, And More
In April 2021, HealthReach Community Health Centers in Waterville, Maine, notified over...
Global IT Compliance: How to Stay Audit-Ready in 2026
IT compliance has become a top-tier challenge for global organizations. The reason isn’t...
Ready to optimize your remote on- and offboardings?
Let’s schedule a short chat and see how we can help!