A Modern Hardware Asset Management Guide for Businesses

IT departments are losing control of their hardware, and the numbers prove it.
Assets vanish, warranties expire, and downtime hits when devices fail mid-project, leaving IT teams scrambling to manage the aftermath.
Even the public sector isn’t immune. In February 2025, New York state auditors found 17,887 government IT devices were marked absent.
Alarmingly, 82% of them had no known location, and staff could not locate 94 of the 102 devices they tried to find in stockrooms.
If you think missing devices only waste money, you’re wrong. Every missing device is also a security threat because it’s susceptible to data leaks.
The Identity Theft Resource Center logged 3,158 U.S. data compromises last year, essentially flat near record highs.
That’s the day-to-day reality for IT: equipment slips off the radar and ghost assets invisibly keep draining resources, and then expose your company to countless security risks.
Hardware asset management helps you solve these common problems.
It introduces clear inventory, faster deployment, clean retirements, and evidence you can hand to an auditor without breaking stride.
With effective HAM, you not only never lose track of assets, you protect both money and sensitive data.
Let’s learn about Hardware Asset Management and how to implement it in your organization.
What is Hardware Asset Management?
Hardware Asset Management (HAM) is the process of managing IT hardware assets from planning to final disposition. It involves building a single, trusted inventory, defining ownership and lifecycle states, and handling every touchpoint.
The process includes procurement, receipt and tagging, deployment and moves, patches and repairs, warranty and contract management, refresh, and certified retirement with data sanitization and chain-of-custody records.
Each asset carries identifiers (such as serial numbers and MAC addresses), ownership and warranty data, security requirements, and a financial footprint throughout its useful life.
Mature HAM also works closely with service desks, CMDBs, and identity and endpoint management tools. That means you detect changes automatically, keep license and support entitlements aligned, track costs and depreciation, and enforce risk controls. The result is less device loss, smoother onboarding, consistent refresh cycles, and audits you can confidently stand behind.
Note: Hardware asset management is exclusive to technological equipment only. Assets such as office furniture, vehicles, and company-issued merchandise fall under the broad category of asset management.
Why Do You Need Lifecycle-Driven HAM?
Business hardware is one of the fastest-depreciating assets a company owns. From the moment it’s unboxed, it loses value, takes daily wear, and demands ongoing maintenance and occasional repairs.
A robust hardware asset management program enables you to extract maximum value from your hardware investments, thereby offsetting the impact of depreciation.
Here are the key benefits of HAM:
- Gives you a trustworthy, real-time inventory. With a HAM system, you always know who has a particular device, where it is, what state it’s in, and which policies apply. That accuracy pays off in audits, chargebacks, and everyday planning.
- Lowers the total cost of ownership. When you have a working, lifecycle-based HAM process, you’ll also benefit from lower maintenance costs, more precise hardware budgets, and reduced spending on unnecessary hardware assets.
- Enables faster onboarding and keeps employees happier. HAM gives new hires the right gear, already set up. With zero-touch provisioning, a simple catalog of approved devices, and the right accessories assigned up front, day one becomes productive.
- Ensures a smaller security impact. Lost, stolen, and unreturned devices can have a profound security impact. Ponemon’s benchmark marks the average cost of a lost or stolen business device at $49,246, with most of that tied to data breach exposure, investigation, and legal risk. With HAM, even if something goes missing, you know exactly what was lost, and you can remotely lock or wipe it through integrated endpoint tools.
- Keeps downtime and disruptions to a minimum. HAM gives you a bird’s eye view of warranties, device health signals, and support tickets so you can act before things break. You can trigger replacements before batteries swell, schedule depot repairs while users keep a loaner, and retire models as failure rates climb.
- Enables clean and compliant end-of-life. A good HAM system helps you dispose of hardware in a compliant and environmentally suitable manner. Some also offer documentation support to help your organization stay compliant with regulatory and ESG expectations.
- Helps with better forecasting, smarter refresh, and tighter budgets. When every request, swap, repair, and return is captured in one place, finance and IT finally work from a single source of truth. That visibility helps plan refreshes around health and warranty windows, buy only what you need, and redeploy idle equipment. Those choices compound into cleaner budgets and steadier spending.
The Hardware Asset Management Lifecycle
HAM involves the entire lifecycle of your organizational assets. This lifecycle is easier to understand if broken into these five parts:
1. Planning and budgeting
This stage sets the foundation for effective hardware asset management.
It revolves around identifying your organization’s technology needs in the context of its overall business goals. A thorough review of existing hardware helps highlight areas where performance, capacity, or compatibility may be falling short.
IT procurement planning also extends to the financial dimension. Budgeting in this phase accounts for the full lifecycle cost of assets, including the purchase price, ongoing maintenance, vendor support, and future upgrades. Together, planning and budgeting establish the strategic direction for the entire hardware lifecycle.
2. Request and fulfillment
Procurement kicks off when the business requests new equipment, whether it’s a batch of laptops, server hardware, or office peripherals like printers. In strong hardware asset management practices, procurement moves beyond scattered emails into a structured, streamlined process.
Standardized catalogs, pre-approved device models, and clear policy rules guide who gets what and under which budget, keeping decisions consistent, reducing risk, and controlling costs. The process wraps up with fulfillment, which includes confirming stock, completing purchases, and recording ownership details as devices enter the inventory system.
3. Deployment
This is the stage where the hardware you procured is put to use, or ‘deployed’.
Here, systems like zero-touch provisioning, golden images, and identity-driven setup move a device from sealed to productive in hours instead of days. When you run consolidated lifecycle services, you’ll see real gains here. IDC found structured device lifecycle programs cut PC lifecycle costs by 37%, which is about $873 per PC, by simplifying deployment and adjacent tasks.
In practice, that looks like pre-config at the depot, autopilot enrollment the moment a device powers on, and instant assignment of security baselines.
4. Monitoring
The monitoring stage begins once hardware is in the field and actively supporting employees. At this point, the focus is all about keeping a close eye on every device.
Asset records reconcile with endpoint management, identity, and network data, creating a real-time picture of who has what, where it is, and whether it’s operating as expected.
Monitoring captures more than performance. During this stage, lifecycle states become especially important. Devices constantly move between being new, in use, loaned out, under repair, or nearing retirement.
By linking alerts to these states, the inventory shows the real condition of hardware rather than a static list.
This real-time visibility does more than keep your records clean. It strengthens security, ensures audit readiness, and enables IT to forecast future needs accurately. Most importantly, it reduces downtime by catching problems early before they impact employee productivity.
5. Service and maintenance
Even the best hardware needs care. Break and fix repairs, OS updates, battery swaps, and accessory replacements are inevitable parts of the hardware lifecycle.
Mature HAM routes all of it through clear SLAs and automated workflows. If something breaks, the process should be seamless: log a ticket, ship a loaner device, capture the failing asset, and update the inventory record.
Why is this discipline important? Because downtime is expensive. Industry data pegs the average cost of downtime at around $9,000 per minute. That’s a reminder that rapid triage and standard spares can be worth more than squeezing one extra year from an aging laptop. When you smooth your maintenance stage, you reduce disruptions, limit productivity loss, and avoid risky “temporary workarounds” that can turn into long-term security exceptions..
6. Retirement
Retirement marks the final stages of an asset’s life. And it’s where the stakes are highest.
This stage involves recycling, redeploying, or disposing of hardware once it reaches the end of its lifecycle. The focus is on secure data erasure or, when necessary, physical destruction, with proof linked to the asset record. Hardware then moves through certified recycling or resale channels. Each step should be logged with a full chain of custody to maintain audit readiness.
Why the rigor? Because improper disposal can expose sensitive data, this stage demands extra diligence. In a joint Blancco and Ontrack study, 42% of used drives purchased online still contained sensitive information, and 15% exposed Personally Identifiable Information (PII).
If you get retirement right, you also get some value back through buy-back or redeployment, and you can feed insights back into procurement and refresh planning.
How to Implement a Lifecycle-Based HAM Strategy in Your Organization
Each step comes with its own challenges, and managing them manually can be time-consuming, error-prone, and costly.
In this section, we’ll break down the key processes of effective hardware management.
I’ll also show you how an IT hardware lifecycle management solution like Workwize can help automate many of these steps, giving you real-time visibility and control over your assets.
Step 1: Build a procurement strategy
A solid IT hardware management strategy begins at procurement.
It helps you plan out what to buy and how to buy before you move on to managing assets.
With a solid procurement plan, you can prevent random, unmanaged purchases and ensure you're investing in equipment that supports your business goals.
Here’s how to work this part out:
- Figure out the performance and utilization data of your current hardware. Make sure that what you plan to buy supports long-term growth and operational needs.
- From there, create a catalog of hardware models for various roles and departments. Standardization simplifies the purchasing process and significantly reduces the complexity of IT support and maintenance.
- Lastly, establish a documented, transparent process that outlines how employees submit hardware requests, the specific automated approval workflows for different types of assets and costs, and a list of approved vendors. Integrate this process with IT asset management (ITAM) systems from the very beginning.
Ideally, you should outline the acceptable use of company hardware and the security measures that must be in place, like encryption and password requirements. Don’t ignore a formal process for retiring assets.
However, while procurement plays the foundation for everything that follows, you can’t handle all of it manually.
Even if you do, you risk facing inefficiencies, delays, and a lack of visibility into equipment, especially as you scale.
The best way to handle this is by using a dedicated IT Asset Lifecycle Management (ITALM) solution, such as Workwize, that automates and oversees the entire lifecycle of your IT assets, starting with procurement.
Workwize helps you:
- Digitize processes like request submission and multi-level approvals, and even allows your employees to request new hardware from a standardized catalog.
- Automate approval workflows, ensuring that requests are routed to the correct stakeholders without delay, which shortens the time from request to purchase order.
- Procure even high-spec or custom-spec devices without negotiation with multiple vendors, since the platform does all the searches and lookups for you.
- Track every asset from the moment it leaves the vendor till it reaches your warehouse and is added to the inventory.
- Get all equipment delivered within 5-7 business days to employees’ homes, your office, or employee warehouses.
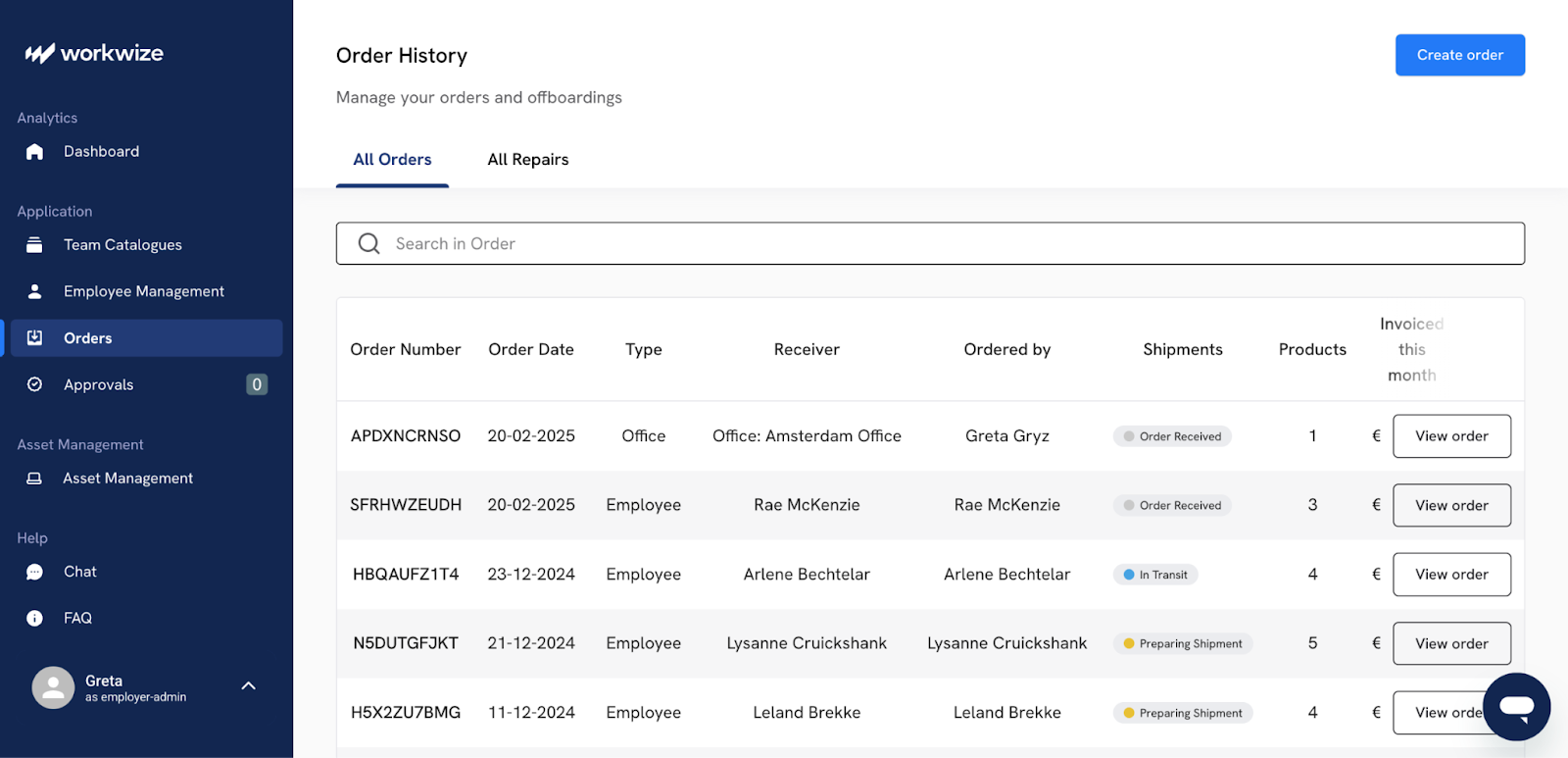
Step 2: Establish a centralized asset repository
Once the devices you need are in your hands, you must build a centralized inventory that records every single asset, both new and existing.
Without a centralized inventory, IT asset tracking becomes chaotic. You’d end up with errors because information is spread across disparate spreadsheets and databases.
This fragmentation leads to ghost assets (items that are on the books but physically missing) and a lack of visibility that hampers decision-making.
A central inventory will give you a real-time view of every asset your organization owns. Here’s how you can do it:
- Compile an initial inventory. This is often the most labor-intensive part of the process. You need to account for every piece of hardware, from servers and laptops to printers and mobile devices.
- Define important data points. For each asset, record essential information like the asset tag, serial number, model, purchase date, location, assigned user, and current status.
However, building this inventory is arguably the most challenging part. If you’re using a spreadsheet or even a manual tracking tool, you have to register every single asset and its details by hand, which is tedious and time-consuming. Moreover, it is not a scalable or reliable long-term solution.
For that reason, using ITALM solutions like Workwize helps you keep track of all IT equipment, centralize all asset information, track them in real time, and alert you if something goes missing.
Workwize also:
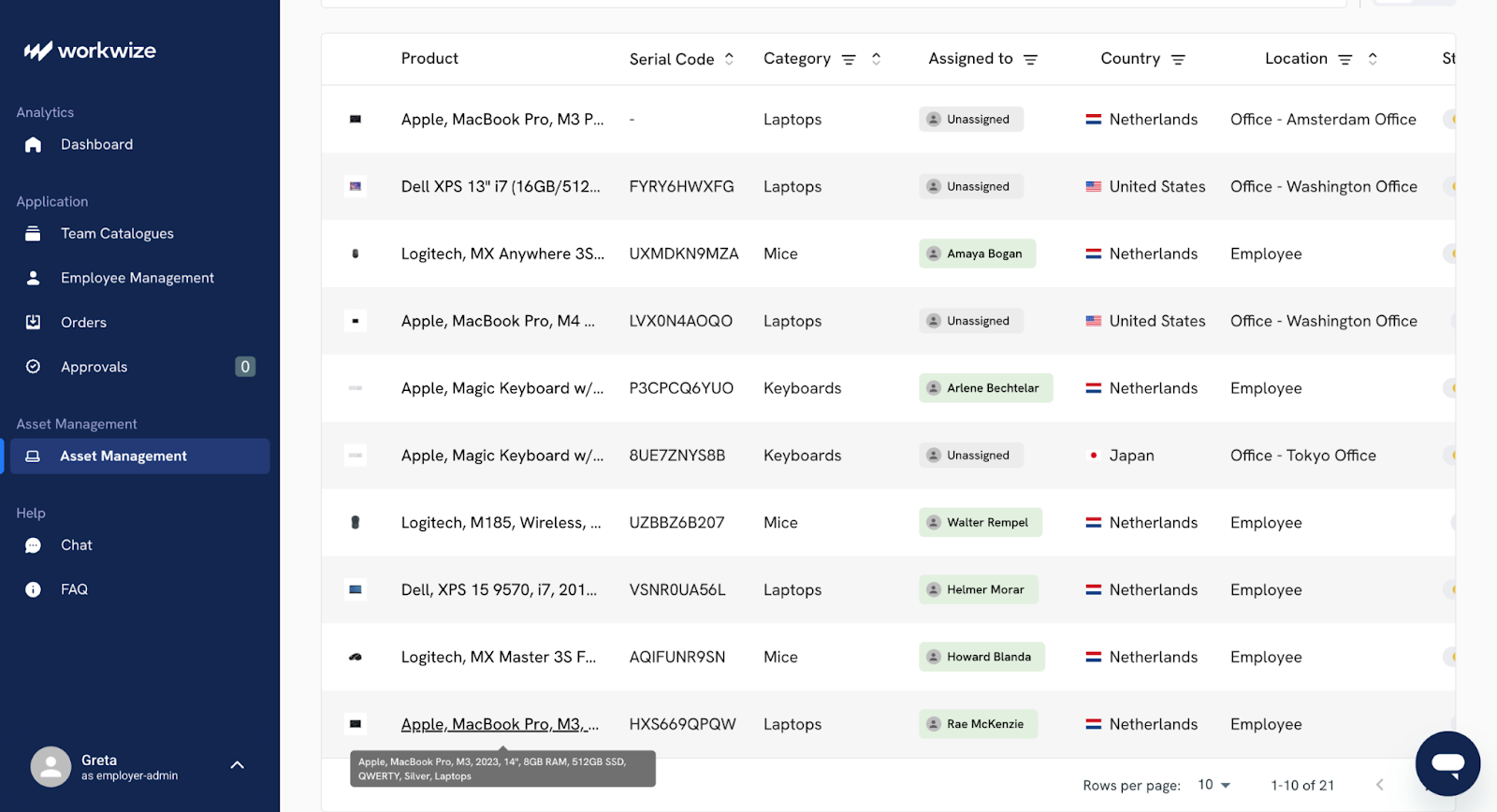
- Gives you a complete, automatically discovered view of all hardware and software assets in a single dashboard.
- Keeps track of assets as they move throughout your organization, and records a chain-of-custody for compliance requirements.
- Alerts you when you are running low on some asset stock, and also when you overpurchase assets. This keeps overstocking and outages to a minimum.
- Lets you track and manage not only hardware but also warranty information, service contracts, and software licenses with automated alerts for expirations.
- Monitors the physical location, uptime, and status of hardware and easily checks assets in or out to employees.
Step 3: Deploy and configure the hardware
Once you have the new assets and the rules governing them, the next step is to get them up and running.
Device deployment is the process of getting new hardware into the hands of employees and making it ready for immediate use. This includes activities like installing the OS, apps, and security configurations needed for the device to be a secure, compliant, and productive tool.
A sloppy deployment will cause security gaps, configuration errors, and a frustrating first-day experience for the user, so don’t skimp here.
Here’s what a smooth deployment process looks like for assets like laptops and workstations:
- Preparation and shipping: After receiving the hardware, physically prepare the device, which can include imaging it with your company's standard software build, and securely ship it to the user's office or home.
- Installation and policy enforcement: For this, you’ll need an MDM. An MDM platform like Kandji or JumpCloud lets you remotely push the required software, configure settings, and enforce security policies automatically. It ensures the device is compliant with password requirements, data encryption is enabled, and all necessary security software is functioning properly when the user receives it.
- User onboarding: Finally, confirm the user has received the device and can access it. Provide clear instructions and resources to help them get started, along with contact information for IT support should they encounter any issues.
While this process is much simpler for peripherals like monitors or keyboards, endpoints like laptops and phones demand a carefully managed deployment.
But how do you deploy devices at scale?
Organizations traditionally rely on manual deployment, where IT technicians physically unbox and configure each device individually. This is incredibly time-consuming and resource-intensive, and also leads to inconsistent configurations and security vulnerabilities.
How do you tackle this? By using an ITALM solution like Workwize, our IT asset management tool.
Workwize can make the deployment process smooth and scalable, essentially just a plug-and-play affair, and ensure that every device is perfectly configured and ready for work from the moment it arrives. It:
- Enables zero-touch provisioning, integrating with device management and vendor programs like Apple Business Manager or Windows Autopilot. This means you can ship devices directly from the vendor to the end-user.
- Works with your existing MDM to centralize mobile device updates, patching, and security releases in a single unified dashboard.
- Automatically enrolls devices in the company’s management system through integrations with HR systems when the employee unboxes the device and connects it to the internet for the first time.
- Downloads all necessary applications, policies, and security settings are pushed to the device remotely without any manual intervention from IT.
Step 4: Actively track, maintain, and optimize your assets
Once a device is in an employee's hands, you have to shift the focus to managing the devices through their active life.
Here, you aim to maximize the asset's value, security, and performance throughout its operational life.
Unique tags like an RFID, QR, or GPS-based sensor will come in handy now. These tags and sensors enable continuous tracking, not just of the asset's physical location, but also its assigned user, status, and any changes made to its hardware.
Management is also a lot about preventive maintenance. Instead of waiting for hardware to fail, schedule \regular maintenance to prevent downtime and extend the life of your assets.
Here’s how it’s best done:
- Schedule regular maintenance. Create a quarterly or biannual schedule for routine servicing and updates.
- Track warranty information. Store warranty and maintenance contract details within your HAM system. Automated alerts can notify you before a warranty expires, allowing you to make informed decisions about renewals or replacements.
- Use data to plan for hardware refreshes. A proper HAM system shall be able to produce the data needed to forecast future hardware needs and plan for hardware refreshes. By analyzing asset age, performance, and maintenance history, you can replace aging hardware before it impacts productivity.
Again, an asset lifecycle solution excels at all of these and lets you automate device management. Here’s how Workwize does it:
- Centralized device control: Take critical actions like pushing software, remotely wiping lost devices, or scheduling retrievals from one place.
- Real-time performance monitoring: Integrates with endpoint management to track hardware health, including CPU, memory, and storage, ensuring smooth operations.
- Automated maintenance management: Tracks warranties, service contracts, and repair history while scheduling maintenance with minimal disruption.
- Smart alerts and optimization: Sends automated alerts for stock, malfunctions, or security issues, and highlights underutilized devices for reallocation.
These features and capabilities enabled by ITALM solutions compound to maximize the ROI for your entire hardware infrastructure while keeping disruptions to a minimum.
Step 5: Retire devices with secure and certified disposal
This is the final step in the hardware lifecycle journey. As you know, you can’t just simply unplug old equipment and stick it in a storage closet. Every asset that comes in must also go out in a way that is secure, compliant, and responsible.
Failing to dispose of equipment properly can lead to data breaches from leftover sensitive information and environmental fines for not following e-waste regulations.
Here’s how to handle this final phase correctly:
- Retrieve the assets. Provide employees with prepaid shipping labels or schedule courier pickups to simplify returns. Use a tracking system so both sides can confirm when devices are received.
- Sanitize the data. Before a device leaves your control, its data must be permanently destroyed. Common methods include NIST 800-88 compliant data wiping, degaussing, or physical destruction like shredding.
- Donate, resell, or recycle. Once the data is gone, you have a few options. If the hardware still has value, it can be refurbished and resold or donated to a charitable organization. If it's truly at the end of its life, it must be recycled responsibly through a certified e-waste partner to prevent harmful materials from ending up in landfills.
To learn more about how to dispose of equipment safely, check our guide on IT asset disposal.
ITALM solutions, such as Workwize, are built to simplify the asset retirement process. Here’s how:
- When an employee leaves, Workwize can kick off an automated collection process. We assess and record a device's condition, and able devices are added back to the available inventory. This makes it convenient to reconfigure and redeploy the hardware.
- You also get the option to recycle or sell devices at the best possible rates.
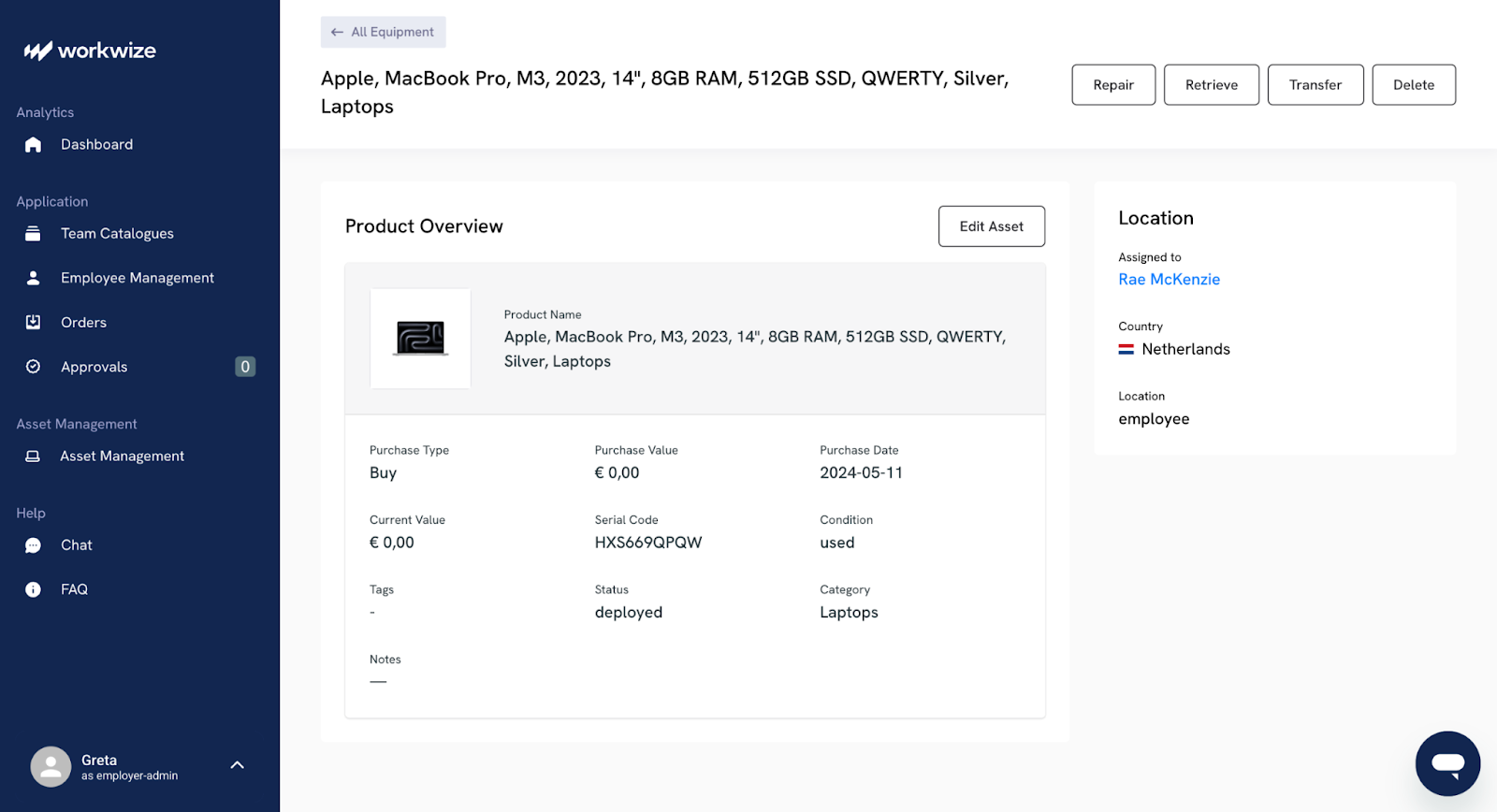
- For assets that cannot be redeployed, Workwize manages the disposal process through certified ITAD partners, giving you a certificate of destruction for every device.
In a nutshell, Workwize helps you manage every step of the asset lifecycle with full control and visibility.
4 Hardware Asset Management Best Practices to Complement Your Strategy
Alright, you’ve got the fundamentals of HAM. You know what it is, you understand the lifecycle, and you're sold on the benefits.
But how do you make your HAM strategy stand out?
Here are four unconventional but incredibly helpful best practices:
Embrace the circular economy by reusing your old assets
Let's be honest, the traditional take-make-dispose model of IT is incredibly wasteful. A more forward-thinking approach is to embrace the principles of a circular economy. This means shifting your mindset from seeing old hardware as a liability to viewing it as a resource.
Instead of just recycling, think about how you can extend the life of your assets.
Look for opportunities: can that old PC be refurbished and redeployed to a less demanding role? Can retired servers be used for spare parts?
Prioritize reuse and refurbishment to not only reduce e-waste but also extract the maximum value from your initial investment.
However, be aware of the difference between usable and unusable devices; some are beyond refurbishment.
Don’t go saving every single device, even the broken ones (source)
Partner with a certified IT Asset Disposition (ITAD) vendor that specializes in refurbishment and resale. They can help you identify assets with remaining value and manage the process of securely wiping data and preparing them for a second life. Even better, this approach can generate revenue for you.
Inject some gamification elements into your HAM processes
Nobody gets excited about updating asset records. So, why not make it a little more interesting? Gamification applies game-like elements such as points, badges, and leaderboards to routine processes to boost participation and make them more engaging.
Imagine a dashboard where each department sees how they rank on returning unused hardware or reporting lost devices promptly. Suddenly, asset management isn’t a boring checklist; it’s become friendly competition.
Gamification creates a healthy and engaging work environment (source)
You have to start small. Create a simple leaderboard to track which teams are most compliant with HAM policies. Offer small, fun rewards for top performers, like a team lunch or a shout-out in the company newsletter.
Gamification turns asset management into a shared responsibility and keeps everyone engaged without heavy-handed enforcement. Over time, you’ll notice faster returns, fewer ghost assets, and a healthier, more collaborative culture around IT hygiene.
Establish a hardware buy-back program
What if you could get cash back for your old, outdated equipment? That's the idea behind a hardware buy-back program. Many ITAD vendors and even some manufacturers offer to purchase your used enterprise-grade equipment that's still in good condition. This is a fantastic way to recoup some of your initial investment on hardware that no longer meets your organization's needs.
If you procure from a value-added-reseller (VAR), check with them as they might already have a buy-back program:
Even some VARs have buy-back programs (Source)
These programs also ensure that your old devices are securely sanitized of all data and responsibly recycled or resold, helping you meet your data security and environmental goals. Just be sure to choose a partner that provides transparent reporting and certificates of data destruction.
Create cross-functional HAM teams
Hardware asset management isn't just an IT problem; it's a business-wide priority.
Every laptop, server, and docking station carries financial, security, and operational implications. That’s why finance, procurement, IT, and even business unit leads should all have a seat at the table.
With cross-functional teams, you can break down the traditional wall that often obstructs effective communication and collaboration.
Departmental collaboration can save you from losses (source)
For example, having someone from finance on the team can provide insights into depreciation schedules and the total cost of ownership, while a representative from a key department can offer feedback on the real-world performance of different hardware models.
This isn’t difficult either: identify key stakeholders from different departments who are impacted by hardware decisions. Or even form a dedicated HAM committee that meets regularly to discuss challenges, review policies, and plan for future needs.
Take Control of Hardware Asset Management With Workwize
Managing hardware is one of the biggest responsibilities for IT teams. Every device in your company has a lifecycle: it’s purchased, used, updated, and eventually retired.
If that lifecycle isn’t managed with intent, devices are wasted, security gaps appear, and costs quickly spiral.
Hardware asset management gives you control. It ensures every device is tracked, maintained, and retired on time. The result is lower costs, fewer disruptions, and a more reliable IT environment.
Workwize helps you implement a strong hardware asset management plan in your organization by giving you one place to oversee your entire fleet.
You can check device status, push updates, manage retirements, and generate clear reports. Automated alerts help you take action before issues escalate, while real-time dashboards keep your IT ecosystem fully transparent.
With Workwize, you can stop reacting to hardware problems and start running a predictable, efficient asset management program.
FAQs
Isn’t our CMDB (or Excel sheet) enough?
Not quite. A CMDB is a logical map of services and configuration items; a spreadsheet is a static snapshot.
HAM is the day-to-day record that tracks all requests, approvals, purchasing, tagging, deployment, repairs, returns, and disposition, tracing them back to people, policies, and cost centers. It integrates with your CMDB, service desk, endpoint manager, and finance, so updates flow automatically.
What metrics show HAM is working?
You don’t have to track everything; just a small set of numbers is good enough:
- Inventory accuracy (% of devices reconciled across tools)
- Time to fulfill a standard device request
- First-day readiness rate for new hires
- Mean Time to Repair (with loaner coverage %)
- Verified data-erasure rate at retirement
Keep them visible. If these trends go the right way, tickets fall, audits go by smoothly, and budgets stop leaking.
Are we going to get locked into Workwize?
No. Workwize is designed to integrate with the tools you already use rather than lock you into a rigid system. You can connect it to your existing MDM and endpoint management platforms, sync data across your IT ecosystem, and export reports whenever needed. If your needs change in the future, your data stays portable and accessible.
About the authors:
Simplify IT operations with Workwize
Learn how Workwize makes IT asset management easier and more efficient. Schedule a custom demo today and see the difference.
Recent articles
Hardware-as-a-Service: 2026 Updated Guide
Imagine you are a 300-employee software development company proliferating and planning to...
15 Best IT Hardware Inventory Management Software in 2026
Tired of being buried under a mountain of sheets to track your organization's IT assets like...
The Ultimate IT Hardware Deployment Guide For 2026
Remote work has popularized fun (read: unsupervised) work environments and cloud tools.
Ready to optimize your remote on- and offboardings?
Let’s schedule a short chat and see how we can help!